Field of the Disclosure
Systems and methods are disclosed which generally relate to raising capital by offering equity positions in intellectual property-backed securities.
Background
Traditionally, investors have been able to invest capital in collective ventures such as corporations by buying shares of the entire company. For example, someone interested in investing in the movie industry was able to buy shares in large corporations that produced movies, such as Sony or Disney. However, these large corporations have other ventures outside of movies that may not be of interest to individual investors. In some instances, an investor may wish to invest in a more targeted manner.
It may be desirable to offer intellectual property-backed securities that allow investment in specific portions of a large company’s total structure, such as investing in specific works such as one movie, one patent, one song, one book, or one design, or bundles of related works. Such creative works are recognized under the umbrella term of intellectual property as activities that inherently carry property rights that can be valued and protected under copyright, patent and trademark laws.
Up until to now, securitizing intellectual property only meant using it as collateral for loans or bonds. For example, Bowie bonds, also known as Pullman bonds, were asset-backed securities which used the current and future revenue from albums recorded by musician David Bowie as collateral. Although collateralized by intellectual property, the bonds were structured as typical bonds with a fixed interest rate and payment schedule.
It is desirable to offer other ways for investing in specific intellectual property.
Summary
Provided is a security backed by one or a plurality of intellectual property preferably selected from patents, movies, printed works, songs and designs, wherein the security comprises a pass-through security that pays a portion of the royalty or licensing fee to the holder of the security as royalty the royalty or licensing fee is received by the issuer of the security.
Provided is an intellectual property security (IPS) comprising investment shares backed by one or a plurality if intellectual property assets providing a defined payout to investors based on the royalty stream associated with the intellectual property asset or assets.
Embodiments of the intellectual property security include those wherein the intellectual property assets are selected from patents, movies, printed works, songs and designs, preferably movies.
Also provided is a method for providing an intellectual property security, the method comprising: defining an offering for sale of investment shares backed by one or a plurality if intellectual property assets; receiving bids from investors for purchase of the investment shares; accepting the bids from investors; tracking revenue associated with the intellectual property assets; and paying the investors a portion of the revenue as it is received.
Embodiments of the method included those wherein the intellectual property assets are selected from patents, movies, printed works, songs and designs, preferably movies.
Also provided is a system comprising a computerized system with hardware and specialized software components for developing, executing and administering intellectual property securities, the system comprising a non-transitory computer readable storage medium comprising a plurality of computer readable instructions embodied thereon which, when executed by the computerized system, causes the computerized system to: define an offering for sale of investment shares backed by one or a plurality if intellectual property assets; receive bids from investors for purchase of the investment shares; accept the bids from investors; track revenue associated with the intellectual property assets; and pay the investors a portion of the revenue as it is received.
Embodiments of the system included those wherein the intellectual property assets are selected from patents, movies, printed works, songs and designs, preferably movies.
Also provided is a non-transitory computer readable storage medium comprising a plurality of computer readable instructions embodied thereon wherein the instructions, when executed by a computerized system with hardware and specialized software components for developing, executing and administering intellectual property securities, cause the computerized system to: define an offering for sale of investment shares backed by one or a plurality if intellectual property assets; receive bids from investors for purchase of the investment shares; accept the bids from investors; track revenue associated with the intellectual property assets; and pay the investors a portion of the revenue as it is received.
Embodiments of the non-transitory computer readable storage medium included those wherein the intellectual property assets are selected from patents, movies, printed works, songs and designs, preferably movies.
Brief Description of the Drawings
The disclosed aspects will hereinafter be described in conjunction with the appended drawings, provided to illustrate and not to limit the disclosed aspects, wherein like designations denote like elements.
FIG. 1 depicts a schematic chart of securities according to an exemplary embodiment of the disclosed subject matter.
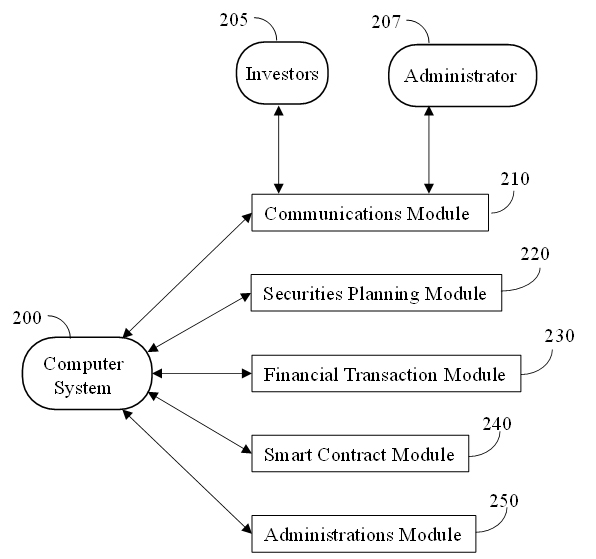
FIG. 2 depicts a schematic functional diagram of a computer system relating to planning and developing securities, modeling and evaluating alternatives, as well as executing and administering an offering for sale of securities according to an exemplary embodiment of the disclosed subject matter.
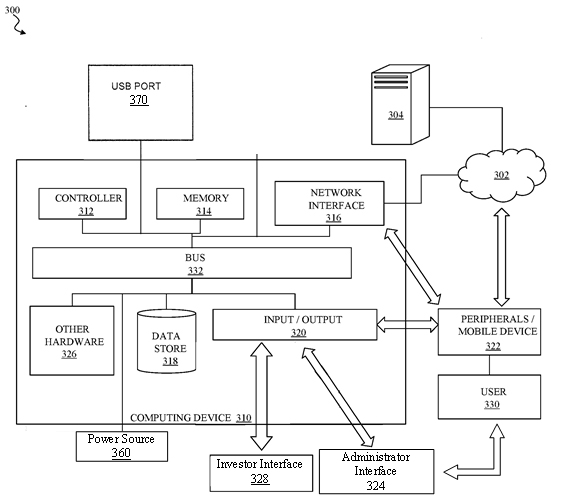
FIG. 3 depicts a functional diagram of components of a computer system according to an exemplary embodiment of the disclosed subject matter.
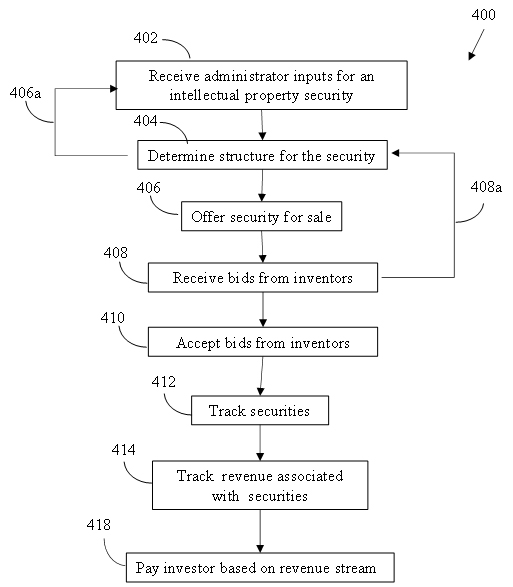
FIG. 4 shows a process flow diagram for defining, offering for sale and administering an intellectual property security according to an embodiment of the disclosed subject matter.
Detailed Description of the Disclosed Subject Matter
In accordance with various embodiments of the invention, and as shown in the figures, various systems and methods are disclosed which generally provide a platform for the creation, communication, price quotation, and execution of trades for specified pools of intellectual property asset-backed securities.
The term Intellectual Property Security relates to the transaction process of securitizing intellectual property. It involves one or more intellectual property assets. It originates with the licensee’s payments, which pass through a collecting society before being released to the investor.
An Intellectual Property Security may be a royalty stream backed by an intellectual property asset such as a movie, a patent, a song, a book, a design or any other registered intellectual property. A servicing intermediary may collect royalty payments from the issuer and, after deducting a small management fee, remits or passes them through to the holders of the intellectual property pass-through security.
Each security can represent from one single intellectual property asset to a large number of intellectual property assets in any combination.
When there is a number of intellectual property assets, these can be of different kinds like the portfolio of rights combined in a movie, including image rights, music rights etc…
Payments are made to investors periodically, corresponding with the payment schedules set in the movie licensing or distribution agreements.
The intellectual property securities systems and methods described herein allow for investment in one or more intellectual properties owned by a company wherein individual investors are able to invest in specific intellectual property owned by a company instead of buying fractional shares in the company.
As illustrated in Figure 1, a company, such as an entertainment-focused corporation 100, may hold a number of ventures, including movies, television (including production and distribution venues such as networks or streaming services), sports teams, electronics and recordings. An investor may purchase fractional shares 110 in the corporation in which the investor receives dividends based on the financial performance of all ventures held by the corporation. Because these ventures may perform with different revenues, profits, expenses, etc. the shares 110 represent a portion of profits weight-averaged across the entire corporation. In an alternative, an investor could invent in a targeted segment of the corporation by buying intellectual property securities 120. In the embodiment shown, the intellectual property securities 120 are based on one or a plurality of movie assets held by the corporation 100.
As shown in FIG. 2A, a computer system 200 is the core element of the intellectual property securities architecture, receiving, generating, storing, integrating and coordinating data required for defining intellectual property receiving investment payments from a plurality of investors 205, matching bets from the plurality of investors, optionally generating smart contracts among investors and the company, determining revenues related to the intellectual properties and administering payouts to investors. The computer system is further provided with at least one processor and into which is loaded software components for receiving informational inputs from the plurality of investors via communications module or interface 210.
Block 210 represents a communication module, which manages inputs from investors and transmits outputs to the investors. Inputs from investors include investing information, investor identity, designation of a payment vehicle or digital “wallet”, such as a credit or debit account, including credit or debit cards issued by a financial institution, Venmo or Pay Pal® apps, etc. Communications module 210 may also be used by administrator(s) 207 of the computer system to communicate with the system. Administrator(s) may provide inputs to the system to maintain and manage the system to make sure it is operating correctly. In embodiments, the administrator(s) 207 may also provide inputs to the system to designate intellectual property assets for investors to invest in, risks assessments, projected revenue streams, etc.
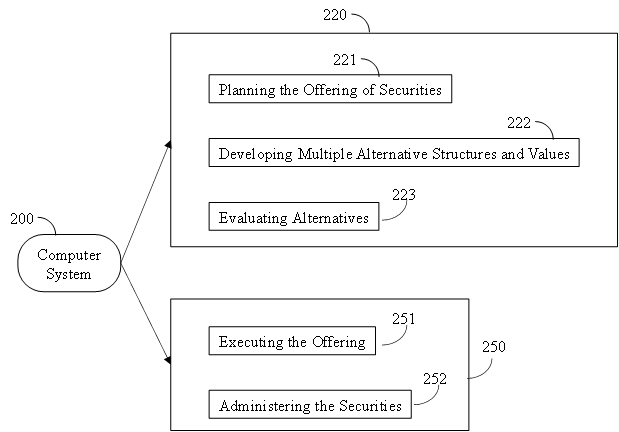
In block 220, the system includes a securities planning module in which the intellectual property securities are defined, as described in greater detail in regard to Figure 2B.
Block 230 comprises the financial transactions module that manages payments from investors to cover their bids, payments to investors and collection of transaction fees. In embodiments, once a bid is accepted, the financial transactions module may withdraw the bid amounts plus transaction fees from investors’ payment vehicles in response to acceptance of bids by the computer system. Block 230 also receives payments from the revenue streams associated with the intellectual property assets backing the intellectual property securities and disburses payments to the investors based on the terms of the intellectual property securities.
In embodiments, the intellectual property securities may be offered in the form of a smart contract, described in greater detail below. In block 240, the smart contract module executes smart contracts by generating data blocks defining the intellectual property securities, including all terms and conditions binding on the investors and the company such as purchase prices, revenue streams from the intellectual properties, percentages of the revenue streams represented by the securities, etc.
Block 250 shows the securities administration module, which executes and administers the intellectual property securities.
As shown in Figure 2B, block 220 comprises aspects of defining the intellectual property security offerings.
In block 221, planning the offering of securities includes establishing the target amount of capital to be raised. Guided by inputs from administrator(s) of the system representing the seller, bank, broker, underwriter and/or other financial institutions, the system conducts feasibility studies for offering intellectual properties to define the structure of the offering. The offering planning includes specific variables to be included, ranges of acceptable values for each variable, and terms and conditions to be included in the offering.
In block 222, the system models and projects multiple values of individual variables and combinations of multiple sets of variables, such as time series projections and economic modeling of interaction between variables.
In block 223, the system evaluates alternatives by reviewing results of modeling and projections. Selecting one or more sets of variables that meet targets will be used to refine the structure and value of variables and terms and conditions for price categories of the intellectual property shares. Additional modeling and projections may be required to define a preferred set of values for the variables and terms and conditions for inclusion in the offering of securities in the price categories of the intellectual property shares. When initiated by the seller, one or more intellectual property securities may be offered as individual or pooled assets. When initiated by a buyer, the buyer may input a desired type of security and the system may generate securities based on the defined characteristics.
Figure 2B also shows block 250 comprising aspects of administering the intellectual property security offerings.
In block 251, the system executes the offering of the securities. The price and content of the individual shares of the price category tranches are established, including definitions of shares of revenues and assets to be included in each tranche. Technical and legal details are finalized and the intellectual property securities are brought to market. The system receives and accepts bids for shares in each intellectual property security from at least one investor, tracks progress of sales of shares within each intellectual property security, and closes sales when target values are met. The system may also receive sell orders from holders of shares and sell them to new investors.
Block 251 may comprise an order creation module. In general, the order creation module may have two modes of functionality. In a first mode, the order creation module permits a buyer to search a database of specified pools and to select one or more pools from the inventory for pricing by a selected group of sellers. It will be understood from the following disclosure that, although multiple pools are selected, and number of pools less than the total number selected (or none at all) may be quoted and ultimately traded. In a second mode, a buyer is provided with the option to select the characteristics of a desired specified pool. These characteristics may be transmitted through system 200 to one or more sellers. The sellers can identify one or more pools in their respective inventories that substantially meet the buyer’s specified set of characteristics or agree to create a specified pool meeting such characteristics.
In operation, by setting various criteria and through selection of one or more sellers, through the operation of the order creation module, buyers can create a customized inventory query which will return available asset-backed securities from database in the system (See Figure 3). In the alternative, the query can be submitted directly to the seller in order to determine whether the seller has or can stipulate to an asset-backed security meeting the buyer’s requirements. This feature may be used when a security meeting the buyer’s requirements is not in the inventory of one or more sellers.
In an alternative embodiment, wherein one or more desired securities are not in an inventory of offered properties, a buyer may be enabled to send an inquiry message to one or more sellers inquiring as to the availability of a security meeting the buyer’s needs. In this embodiment, a buyer typically creates an order query using system 200’s order creation module to determine whether the desired security is listed in the system’s database of securities previously populated by one or more sellers Such query details may include, title(s) or other identifier(s) of assets, a pool number of an asset pool, a weighted average maturity, a constant payment rate, an originator identifier, etc. While the buyer may use various inventory filters to enable the buyer to search for mortgage-backed securities meeting defined criteria, in some instances, the desired security may not be available. In those instances, the buyer can define the criteria according to which an inquiry message will be generated and transmitted to one or more sellers. A dealer list may include a list of dealers, acting as sellers, and aspects of the buyer interface enable the buyer to select the dealers to which the inquiry message will be transmitted. Once the buyer completes the process of inputting desired criteria and selecting dealers, the criteria and dealer data is transmitted to and received by system 200. System 200 then generates an inquiry message which includes the characteristics for the pool of assets defined by the buyer. The data in the inquiry message is then transmitted to the selected dealer(s).
In block 252, the system administers the securities (shares) in the offering. It maintains detailed and current records of individual investor accounts as required for periodic and cumulative payments, tax treatment, benefits, reports and other purposes. It maintains required and useful records related to financial analysis and financial reports of investors, brokers, and other involved parties.
In embodiments, the offering, sale and administration of the intellectual property securities may be conducted as a smart contract.
A smart contract is a computer application simulating the operation of a contract. It is a computer program or a transaction protocol which is intended to automatically execute, control or document legally relevant events and actions according to the terms of a contract or an agreement between or among parties. The objectives of smart contracts are the reduction of need in trusted intermediators, arbitrations and enforcement costs, fraud losses, as well as the reduction of malicious and accidental exceptions. The smart contract is stored on a blockchain that runs when predetermined conditions are met. They may be used to automate the execution of an agreement so that all participants can be immediately certain of the outcome, without any intermediary’s involvement or time loss.
The reliability of the smart contract comes from its automaticity which gives it a power of execution unmatched to date.
A smart contract also can be regarded as a secured stored procedure as its execution and codified effects like the transfer of some value between parties are strictly enforced and cannot be manipulated, after a transaction with specific contract details is stored into a blockchain or distributed ledger. That is because the actual execution of contracts is controlled and audited by the platform, not by any arbitrary server-side programs connecting to the platform. Smart contracts are particularly useful for managing exchanges of virtual financial or value assets, where no tangible materials need to be moved.
The contracting parties program the contractual terms, payments to be made and all dispatches of documents used for the execution of the contract in the software application and may no longer retract their commitments. Once launched, the application performs the scheduled operations without human intervention, as scheduled.
End clients interact with a smart contract through transactions. Such transactions with a smart contract can invoke other smart contracts. These transactions might result in changing the state and sending financial assets from one smart contract to another or from one account to another. Financial assets can include nationally denominated currencies, cryptocurrencies, virtual stock certificates, or other asset whose value can be defined digitally.
Similar to a transfer of value on a blockchain, deployment of a smart contract on a blockchain occurs by sending a transaction from a wallet for the blockchain. The transaction includes the compiled code for the smart contract as well as a special receiver address. That transaction must then be included in a block that is added to the blockchain, at which point the smart contract’s code will execute to establish the initial state of the smart contract. Byzantine fault-tolerant algorithms secure the smart contract in a decentralized way from attempts to tamper with it. Once a smart contract is deployed, it cannot be updated. Smart contracts on a blockchain can store arbitrary state and execute arbitrary computations.
The reliability of the intelligent contract can be greatly increased by relying on a decentralized IT environment allowing secure access to the contractors and unfalsifiable by them.
Each smart contract may include information about the investment in the intellectual property security. Such information may include the amount of the investment, the agreed upon payouts, the revenue stream, the time the investment is agreed upon, the identities of the parties, etc. Investment information may further include conditional outcomes based upon each potential outcome, including the facilitation of payment from the seller to the investor, and/or the return of funds in event of a void or cancellation. In some embodiments, a settlement service may be agreed upon between the parties.
Some embodiments provide that the smart contracts may be generated on individual PC’s, on a mobile device and/or in the cloud. Such examples are non-limiting as the smart contracts may be generated at a variety of other devices and/or types thereof. In some embodiments, each smart contract may involve external services at the discretion of the parties. In some embodiments, a range of options may be selected by the parties at the time the smart contract is generated.
Some embodiments provide that a smart contract may be registered with a settlement service provider that is agreed to by the parties. In some embodiments, a settlement service may provide information about the outcome of the intellectual properties on which the security is based. In some embodiments, the settlement service may send the information to the counterparties, which may trigger the payouts under the terms of the smart contract. For example, the settlement service provider may initiate a bank transfer from the seller to the buyer based on the smart contract or from the payer of the revenue (e.g. licensing fee or royalty) directly to the investor. In some embodiments, the process may be automated by software on a computer and/or server controlled by the settlement service. Embodiments herein do not require the funds to be held in any kind of escrow, however, such option is contemplated by this disclosure. For example, embodiments herein are directed to any financial settlement process that may be used in conjunction with the smart contracts as disclosed herein.
Some embodiments provide that the settlement transaction may be stored in blockchain to close the contract. In some embodiments, details corresponding to the settlement transaction may be retained for auditing, later scrutiny and/or to ensure that no errors are made.
FIG. 3 depicts a computer system 300 according to an embodiment of the present disclosure. In general, the computer system 300 may include a computing device 310, such as a special-purpose computer designed and implemented for receiving user inputs, determining and directing and controlling the output of signals. The computing device 310 may be or include data sources, client devices, and so forth. In certain aspects, the computing device 310 may be implemented using hardware or a combination of software and hardware. The computing device 310 may be a standalone device, a device integrated into another entity or device, a platform distributed across multiple entities, or a virtualized device executing in a virtualization environment.
The computing device 310 may communicate across a network 302. The network 302 may include any data network(s) or internetwork(s) suitable for communicating data and control information among participants in the computer system 300. This may include public networks such as the Internet, private networks, and telecommunications networks such as the Public Switched Telephone Network or cellular networks using cellular technology and/or other technologies, as well as any of a variety other local area networks or enterprise networks, along with any switches, routers, hubs, gateways, and the like that might be used to carry data among participants in the computer system 300. The network 302 may also include a combination of data networks and need not be limited to a strictly public or private network.
The computing device 310 may communicate with an external device 304. The external device 304 may be any computer, mobile device such as a cell phone, tablet, smart watch or other remote resource that connects to the computing device 310 through the network 302. This may include any of the servers or data sources described herein, including servers, content providers, databases or other sources for shot information to be used by the devices as described herein.
In general, the computing device 310 may include a controller or processor 312, a memory 314, a network interface 316, a data store 318, and one or more input/output interfaces 320. The computing device 310 may further include or be in communication with peripherals 322 and other external input/output devices that might connect to the input/output interfaces 320.
The controller 312 may be implemented in software, hardware or a combination of software and hardware. According to one aspect, the controller 312 may be implemented in application software running on a computer platform. Alternatively, the controller 312 may include a processor or other processing circuitry capable of processing instructions for execution within the computing device 310 or computer system 300. The controller 312, as hardware, may include a single-threaded processor, a multi-threaded processor, a multi-core processor and so forth. The controller 312 may be capable of processing instructions stored in the memory 314 or the data store 318.
The memory 314 may store information within the computing device 310. The memory 314 may include any volatile or non-volatile memory or other computer-readable medium, including without limitation a Random-Access Memory (RAM), a flash memory, a Read Only Memory (ROM), a Programmable Read-only Memory (PROM), an Erasable PROM (EPROM), registers, and so forth. The memory 314 may store program instructions, program data, executables, and other software and data useful for controlling operation of the computing device 310 and configuring the computing device 310 to perform functions for a user 330. The memory 314 may include a number of different stages and types of memory for different aspects of operation of the computing device 310. For example, a processor may include on-board memory and/or cache for faster access to certain data or instructions, and a separate, main memory or the like may be included to expand memory capacity as desired. All such memory types may be a part of the memory 314 as contemplated herein.
The memory 314 may, in general, include a non-volatile computer readable medium containing computer code that, when executed by the computing device 310 creates an execution environment for a computer program in question, e.g., code that constitutes processor firmware, a protocol stack, a database management system, an operating system, or a combination of the foregoing, and that performs some or all of the steps set forth in the various flow charts and other algorithmic descriptions set forth herein. While a single memory 314 is depicted, it will be understood that any number of memories may be usefully incorporated into the computing device 310.
The network interface 316 may include any hardware and/or software for connecting the computing device 310 in a communicating relationship with other resources through the network 302. This may include remote resources accessible through the Internet, as well as local resources available using short range communications protocols using, e.g., physical connections (e.g., Ethernet), radio frequency communications (e.g., Wi-Fi, Bluetooth), optical communications (e.g., fiber optics, infrared, or the like), ultrasonic communications, or any combination of these or other media that might be used to carry data between the computing device 310 and other devices. The network interface 316 may, for example, include a router, a modem, a network card, an infrared transceiver, a radio frequency (RF) transceiver for receiving AM/FM or satellite radio sources, a near field communications interface, a radio-frequency identification (RFID) tag reader, or any other data reading or writing resource or the like.
The network interface 316 may include any combination of hardware and software suitable for coupling the components of the computing device 310 to other computing or communications resources. By way of example and not limitation, this may include electronics for a wired or wireless Ethernet connection operating according to the IEEE 802.11 standard (or any variation thereof), or any other short or long range wireless networking components or the like. This may include hardware for short range data communications such as Bluetooth or an infrared transceiver, which may be used to couple to other local devices, or to connect to a local area network or the like that is in turn coupled to a data network 302 such as the Internet. This may also include hardware/software for a WiMax connection or a cellular network connection (using, e.g., CDMA, GSM, LTE, or any other suitable protocol or combination of protocols). The network interface 316 may be included as part of the input/output devices 320 or vice-versa.
The data store 318 may be any internal or external memory store providing a computer-readable medium such as a disk drive, an optical drive, a magnetic drive, a flash drive, or other device capable of providing mass storage for the computing device 310. The data store 318 may store computer readable instructions, data structures, program modules, and other data for the computing device 310 or computer system 300 in a non-volatile form for relatively long-term, persistent storage and subsequent retrieval and use. For example, the data store 318 may store an operating system, application programs, program data, databases, files, and other program modules or other software objects and the like.
As used herein, processor, microprocessor, and/or digital processor may include any type of digital processing device such as, without limitation, digital signal processors (“DSPs”), reduced instruction set computers (“RISC”), complex instruction set computers (“CISC”) processors, microprocessors, gate arrays (e.g., field programmable gate arrays (“FPGAs”)), programmable logic device (“PLDs”), reconfigurable computer fabrics (“RCFs”), array processors, secure microprocessors, and application-specific integrated circuits (“ASICs”). Such digital processors may be contained on a single unitary integrated circuit die or distributed across multiple components.
As used herein, computer program and/or software may include any sequence or human or machine cognizable steps which perform a function. Such computer program and/or software may be rendered in any programming language or environment including, for example, C/C++, C#, Fortran, COBOL, MATLAB™, PASCAL, GO, RUST, SCALA, Python, assembly language, markup languages (e.g., HTML, SGML, XML, VoXML), and the like, as well as object-oriented environments such as the Common Object Request Broker Architecture (“CORBA”), JAVA™ (including J2ME, Java Beans, etc.), Binary Runtime Environment (e.g., “BREW”), and the like.
The input/output interface 320 may support input from and output to other devices that might couple to the computing device 310. This may, for example, include serial ports (e.g., RS-232 ports), universal serial bus (USB) ports, optical ports, Ethernet ports, telephone ports, audio jacks, component audio/video inputs, HDMI ports, and so forth, any of which might be used to form wired connections to other local devices. This may also include an infrared interface, RF interface, magnetic card reader, or other input/output system for wirelessly coupling in a communicating relationship with other local devices. It will be understood that, while the network interface 316 for network communications is described separately from the input/output interface 320 for local device communications, these two interfaces may be the same, or may share functionality, such as where a USB port 370 is used to attach to a Wi-Fi accessory, or where an Ethernet connection is used to couple to a local network attached storage. The input/output interface 320 may further output signals to displays of peripheral devices, as described herein.
As used herein, a user 330 is any human that interacts with the computer system 300. In this context, a user may be generally classed within one of two categories. One category is an administrator of the system, representing the seller and/or financial institution organizing and conducting the offering of the intellectual property security. Another category is an investor who buys and sells shares in the intellectual property security.
In certain embodiments the I/O interface 320 facilitates communication with input and output devices for interacting with a user. For example, the I/O interface may communicate with one or more devices such as a user-input device and/or a display 350 which may be instantiated on the device described herein or on a separate device such as a mobile device 208, which enable a user to interact directly with the controller 312 via bus 332. The user-input device may comprise one or more push-buttons, a touch screen, or other devices that allows a user to input information. In these embodiments, the computer system may further comprise a display to provide visual output to the user. The display may comprise any of a variety of visual displays, such as a viewable screen, a set of viewable symbols or numbers, and so on. One can appreciate that the inputs and outputs of the computer system would be different for administrators and investors. Accordingly, the computing device 310 may communicate administrators and investors with different interfaces 324 and 328.
A peripheral 322 may include any device used to provide information to or receive information from the computing device 310. This may include human input/output (I/O) devices such as a keyboard, a mouse, a mouse pad, a track ball, a joystick, a microphone, a foot pedal, a camera, a touch screen, a scanner, or other device that might be employed by the user 330 to provide input to the computing device 310. This may also or instead include a display, a printer, a projector, a headset or any other audiovisual device for presenting information to a user. The peripheral 322 may also or instead include a digital signal processing device, an actuator, or other device to support control of or communication with other devices or components. In one aspect, the peripheral 322 may serve as the network interface 316, such as with a USB device configured to provide communications via short range (e.g., Bluetooth, Wi-Fi, Infrared, RF, or the like) or long range (e.g., cellular data or WiMax) communications protocols. In another aspect, the peripheral 322 may augment operation of the computing device 310 with additional functions or features, or other device. In another aspect, the peripheral 322 may include a storage device such as a flash card, USB drive, or other solid-state device, or an optical drive, a magnetic drive, a disk drive, or other device or combination of devices suitable for bulk storage. More generally, any device or combination of devices suitable for use with the computing device 310 may be used as a peripheral 322 as contemplated herein.
Other hardware 326 may be incorporated into the computing device 310 such as a coprocessor, a digital signal processing system, a math co-processor, a graphics engine, a video driver, a camera, a microphone, additional speakers, and so forth. The other hardware 326 may also or instead include expanded input/output ports, extra memory, additional drives, and so forth.
A bus 332 or combination of busses may serve as an electromechanical backbone for interconnecting components of the computing device 310 such as the controller 312, memory 314, network interface 316, other hardware 326, data store 318, and input/output interface. As shown in the figure, each of the components of the computing device 310 may be interconnected using a system bus 332 in a communicating relationship for sharing controls, commands, data, power, and so forth.
The computing device 310 is connected to a power source 360 to provide electrical power for the computing device to run.
The various illustrative logical blocks, modules and circuits described in connection with the present disclosure may be implemented or performed with a processor specially configured to perform the functions discussed in the present disclosure. The processor may be a neural network processor, a digital signal processor (DSP), an application specific integrated circuit (ASIC), a field programmable gate array signal (FPGA) or other programmable logic device (PLD), discrete gate or transistor logic, discrete hardware components or any combination thereof designed to perform the functions described herein. Alternatively, the processing system may comprise one or more neuromorphic processors for implementing the neuron models and models of neural systems described herein. The processor may be a microprocessor, controller, microcontroller, or state machine specially configured as described herein. A processor may also be implemented as a combination of computing devices, e.g., a combination of a DSP and a microprocessor, a plurality of microprocessors, one or more microprocessors in conjunction with a DSP core, or such other special configuration, as described herein.
The steps of a method or algorithm described in connection with the present disclosure may be embodied directly in hardware, in a software module executed by a processor, or in a combination of the two. A software module may reside in storage or machine readable medium, including random access memory (RAM), read only memory (ROM), flash memory, erasable programmable read-only memory (EPROM), electrically erasable programmable read-only memory (EEPROM), registers, a hard disk, a removable disk, a CD-ROM or other optical disk storage, magnetic disk storage or other magnetic storage devices, or any other medium that can be used to carry or store desired program code in the form of instructions or data structures and that can be accessed by a computer. A software module may comprise a single instruction, or many instructions, and may be distributed over several different code segments, among different programs, and across multiple storage media. A storage medium may be coupled to a processor such that the processor can read information from, and write information to, the storage medium. In the alternative, the storage medium may be integral to the processor.
The methods disclosed herein comprise one or more steps or actions for achieving the described method. The method steps and/or actions may be interchanged with one another without departing from the scope of the claims. In other words, unless a specific order of steps or actions is specified, the order and/or use of specific steps and/or actions may be modified without departing from the scope of the claims.
The functions described may be implemented in hardware, software, firmware, or any combination thereof. If implemented in hardware, an example hardware configuration may comprise a processing system in a device. The processing system may be implemented with a bus architecture. The bus may include any number of interconnecting buses and bridges depending on the specific application of the processing system and the overall design constraints. The bus may link together various circuits including a processor, machine-readable media, and a bus interface. The bus interface may be used to connect a network adapter, among other things, to the processing system via the bus. The network adapter may be used to implement signal processing functions. For certain aspects, a user interface (e.g., keypad, display, mouse, joystick, etc.) may also be connected to the bus. The bus may also link various other circuits such as timing sources, peripherals, voltage regulators, power management circuits, and the like, which are well known in the art, and therefore, will not be described any further.
The processor may be responsible for managing the bus and processing, including the execution of software stored on the machine-readable media. Software shall be construed to mean instructions, data, or any combination thereof, whether referred to as software, firmware, middleware, microcode, hardware description language, or otherwise.
In a hardware implementation, the machine-readable media may be part of the processing system separate from the processor. However, as those skilled in the art will readily appreciate, the machine-readable media, or any portion thereof, may be external to the processing system. By way of example, the machine-readable media may include a transmission line, a carrier wave modulated by data, and/or a computer product separate from the device, all which may be accessed by the processor through the bus interface. Alternatively, or in addition, the machine-readable media, or any portion thereof, may be integrated into the processor, such as the case may be with cache and/or specialized register files. Although the various components discussed may be described as having a specific location, such as a local component, they may also be configured in various ways, such as certain components being configured as part of a distributed computing system.
The machine-readable media may comprise a number of software modules. The software modules may include a transmission module and a receiving module. Each software module may reside in a single storage device or be distributed across multiple storage devices. By way of example, a software module may be loaded into RAM from a hard drive when a triggering event occurs. During execution of the software module, the processor may load some of the instructions into cache to increase access speed. One or more cache lines may then be loaded into a special purpose register file for execution by the processor. When referring to the functionality of a software module below, it will be understood that such functionality is implemented by the processor when executing instructions from that software module. Furthermore, it should be appreciated that aspects of the present disclosure result in improvements to the functioning of the processor, computer, machine, or other system implementing such aspects.
If implemented in software, the functions may be stored or transmitted over as one or more instructions or code on a computer-readable medium. Computer-readable media include both computer storage media and communication media including any storage medium that facilitates transfer of a computer program from one place to another.
Further, it should be appreciated that modules and/or other appropriate means for performing the methods and techniques described herein can be downloaded and/or otherwise obtained by a user terminal and/or base station as applicable. For example, such a device can be coupled to a server to facilitate the transfer of means for performing the methods described herein. Alternatively, various methods described herein can be provided via storage means, such that a user terminal and/or base station can obtain the various methods upon coupling or providing the storage means to the device. Moreover, any other suitable technique for providing the methods and techniques described herein to a device can be utilized.
The computer program controls input and operation of the device. The computer program includes at least one code segment stored in or on a computer-readable medium residing on or accessible by the device for instructing the computing elements, and any other related components to operate in the manner described herein. The computer program is preferably stored within the memory and comprises an ordered listing of executable instructions for implementing logical functions in the device. However, the computer program may comprise programs and methods for implementing functions in the device that are not an ordered listing, such as hard-wired electronic components, programmable logic such as field-programmable gate arrays (FPGAs), application specific integrated circuits, or other similar or conventional methods for controlling the operation of electrical or other computing devices.
Similarly, the computer program may be embodied in any computer-readable medium for use by or in connection with an instruction execution system, apparatus, or device, such as a computer-based system, processor-containing system, or other system that can fetch the instructions from the instruction execution system, apparatus, or device, and execute the instructions. The computer-readable medium may even be paper or another suitable medium upon which the program is printed, as the program can be electronically captured, via for instance, optical scanning of the paper or other medium, then compiled, interpreted, or otherwise processed in a suitable manner, if necessary, and then stored in a computer memory.
Figure 4 shows a process flow diagram 400 for defining and offering for sale intellectual property security according to an embodiment of the disclosed subject matter.
The process flow diagram 400 starts at block 402 wherein the computer system receives inputs from administrator(s) representing the seller regarding an intellectual property asset to be offered as described herein. Inputs include a target amount of capital to be raised, information regarding the intellectual property’s current and potential valuation, etc. The intellectual property may be rights to a royalty or revenue stream of a movie or pool of movies.
The computer system determines a structure for the intellectual property security in block 404. The determination of the structure comprises conducting activities in blocks 221, 222 and 223 of Figure 2B. It is to be appreciated that defining the structure of the offering in block 404 may comprise several iterative interactions between the computer system and administrator(s) or seller(s) to define the final structure of the intellectual property security (arrow 406a).
Once the final structure of the offering is determined, the computer system moves to executing the offering (block 251 of Figure 2B) by moving to block 406. Block 406 comprises offering the intellectual property security for sale to potential investors. Block 408 comprises receiving bids for shares from investors. As discussed above, in some embodiments, a buyer may bid on shares of intellectual property assets already offered for sale by the seller, or may enquire about assets not currently offered for sale. In embodiments wherein an investor initiates an enquiry about intellectual property asset(s), the inquiry is directed by the system from the investor into block 402 of the process flow scheme (arrow 408a) for analysis and response from the seller(s). It is to be appreciated that defining the structure of buyer-initiated intellectual properties in block 404 may comprise several iterative interactions among the computer system, investors and administrator(s) or seller(s) (arrows 406a and 408a) to define the final structure of the intellectual property security.
Block 410 comprises accepting the bids from investors. Accepting the bids includes issuing shares to the investors at their bid price(s) and holding them in the computer system. Accepting the bids may also include the system designing investor-initiated queries and submitting them for acceptance by the seller. As described above, acceptance of the bids by sellers may comprise generation of a smart contract that defines the final terms and conditions of the intellectual property security.
The system tracks the sales of intellectual property securities in block 412, including the total number of securities sold, the prices offered in bids and accepted by the computer system and the holders of the securities. The computer system tracks revenues associated with the intellectual property assets and determines whether targets defined in the intellectual property security have been met in block 414. Targets may include revenue from licensing fees, royalties, distribution, placement fees, sales of movie-associated merchandise, etc.
If the computer system determines that the target(s) are reached in block 414, the computer system moves to block 418 and disperses payments to investors based on the terms of the securities.
The system and methods described herein may be used for private offerings, initial public offerings or combinations thereof. For example, intellectual property securities may be offered to a limited number of private venture capital entities.
Claims
- An intellectual property security comprising investment shares backed by one or a plurality if intellectual property assets providing a defined payout to investors based on the royalty stream associated with the intellectual property asset or assets.
- The intellectual property security of claim 1 wherein the intellectual property assets are selected from patents, movies, printed works, songs and designs.
- The intellectual property security of claim 1 wherein the intellectual property assets are selected from movies.
- A method for providing an intellectual property security, the method comprising:
- defining an offering for sale of investment shares backed by one or a plurality if intellectual property assets;
- receiving bids from investors for purchase of the investment shares;
- accepting the bids from investors;
- tracking revenue associated with the intellectual property assets; and
- paying the investors a portion of the revenue as it is received.
- The method of claim 4 wherein the intellectual property assets are selected from patents, movies, printed works, songs and designs.
- The method of claim 4 wherein the intellectual property assets are selected from movies.
- A system comprising a computerized system with hardware and specialized software components for developing, executing and administering intellectual property securities, the system comprising a non-transitory computer readable storage medium comprising a plurality of computer readable instructions embodied thereon which, when executed by the computerized system, causes the computerized system to:
- define an offering for sale of investment shares backed by one or a plurality if intellectual property assets;
- receive bids from investors for purchase of the investment shares;
- accept the bids from investors;
- track revenue associated with the intellectual property assets; and
- pay the investors a portion of the revenue as it is received.
- The system of claim 7 wherein the intellectual property assets are selected from patents, movies, printed works, songs and designs.
- A non-transitory computer readable storage medium comprising a plurality of computer readable instructions embodied thereon wherein the instructions, when executed by a computerized system with hardware and specialized software components for developing, executing and administering intellectual property securities, cause the computerized system to:
- define an offering for sale of investment shares backed by one or a plurality if intellectual property assets;
- receive bids from investors for purchase of the investment shares;
- accept the bids from investors;
- track revenue associated with the intellectual property assets; and
- pay the investors a portion of the revenue as it is received.
- The non-transitory computer readable storage medium of claim 9 wherein the intellectual property assets are selected from patents, movies, printed works, songs and designs.
Abstract
A computerized system with hardware and specialized software components for developing, executing and administering intellectual property securities wherein investors are paid from the royalty stream associated with the intellectual property as the revenues are received.